Creating a trust relationship in ADFS
- Open the ADFS administration snap-in.
- Right-click
Trust Relationships > Relying Party Trusts
and chooseAdd Relying Party Trust.
- On the second screen of the wizard, enter RightScale's SP metadata URL.
- Review the auto-configured settings to ensure they look reasonable
- Save the new trust relationship
- Right-click on the new trust relationship, choose
Properties,
and navigate to theAdvanced
tab- Change
Secure hash algorithm
toSHA-1
- Click
OK
to save the changes
- Change
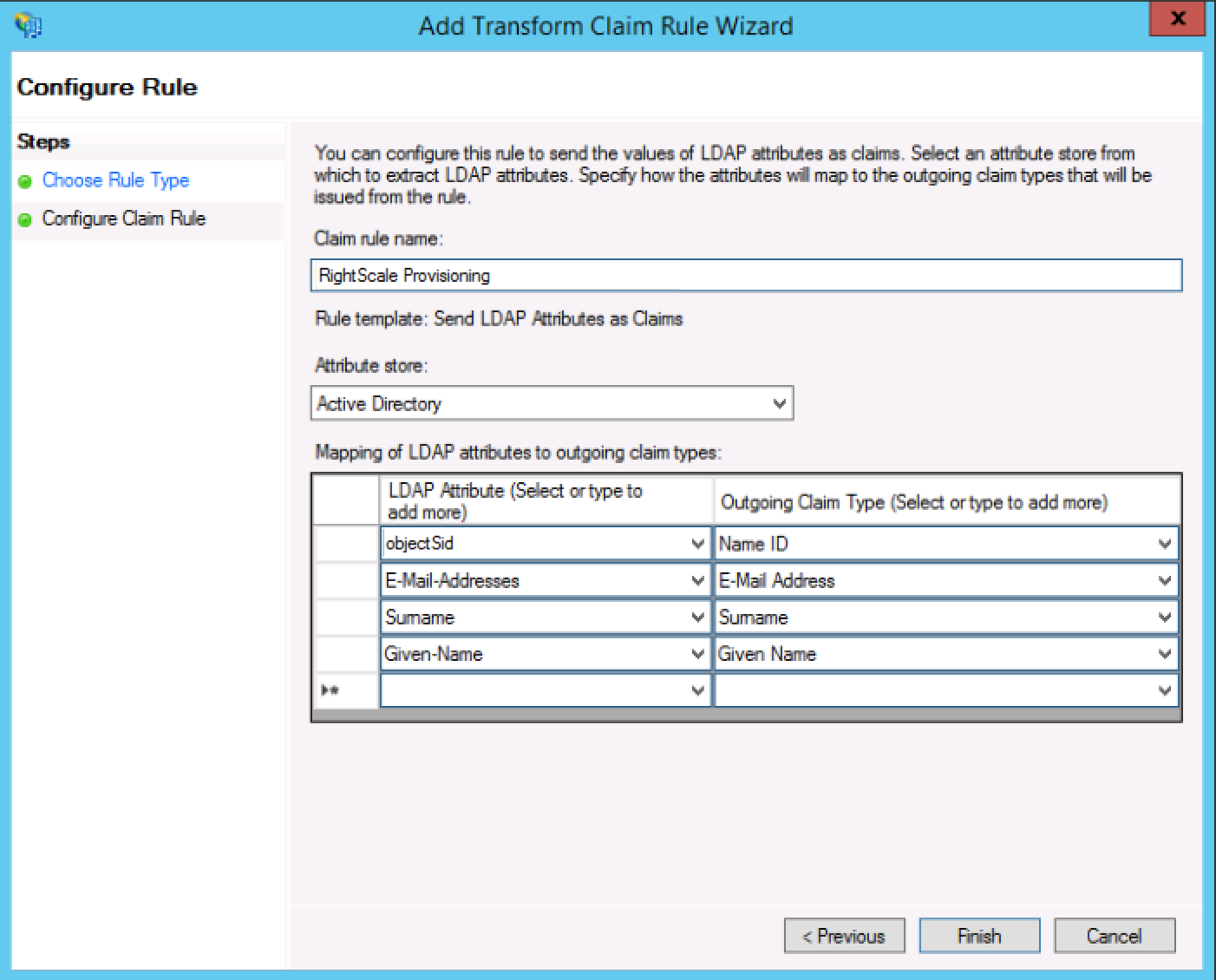
- Add a new transform claim rule for the trust relationship.
- Choose the rule type
Send LDAP attributes as claims
- Choose ActiveDirectory as the attribute store.
- Configure mappings for Name ID and the three RightScale-required attributes as shown in the screenshow below.
- Choose the rule type
Creating a trust relationship in RightScale
In this section, we will set up a trust relationship for ADFS within RightScale. As a result, RightScale will know your identity provider's information, which permits your IdP to initiate logins.
You must have the enterprise_manager
role for the RightScale account you wish to associate with ADFS.
- In a new tab in your browser, navigate to the account you wish to administer in RightScale.
- In the blue nav menu at the top of the screen, select
Settings
and navigate toSingle Sign-on
under theEnterprise
section. (If you do not see this option, then you do not have theenterprise_manager
role for the current account.) - On the resulting page, you should see a list of existing SAML Identity Providers near the top and, above the list, you should see a
New
button. Click theNew
button. In the resulting form, enter the following values:
Input Name Value Display Name Your choice, e.g. MyCompany ADFSLogin Method Leave Allow RightScale-initiated SSO using a discovery hint
uncheckedSAML SSO Endpoint Enter ADFS' SAML request endpoint e.g. https://mycompany.com/adfs/ls/SAML EntityID Enter ADFS' entity ID e.g. http://mycompany.com/adfs/services/trustSAML Signing Certificate Upload the x509 certificate that ADFS uses to sign its SAML assertions Click the
Save
button and you will be returned to the Identity Provider list page. You should see your newly created IdP in this list.Next, click the button to the right to test your IdP configuration. You should be redirected to your IdP where you can log in and complete the SSO login. If you didn't assign the application created when configuring ADFS to your ADFS user, then you will need to do so before completing this step.
Finally, if you wish to have users provisioned via SSO then you will need to Enable authority for your new IdP over the SAML-asserted email domains.
This concludes configuration of your SAML Identity Provider in RightScale. Please continue on to Step 3: Test IdP-Initiated Single Sign-On.